Virtual Private Network
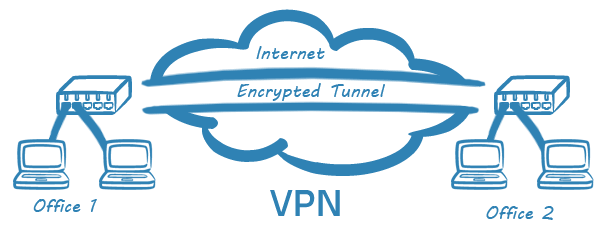
The Virtual Private Network or VPN is changing the way that businesses communicate. Traditionally, in order to deploy a wide area network, organization would need to procure expensive leased line technology to connect their offices. The VPN however has the ability to run over public networks (like the Internet) whilst providing security and integrity for your data.
 The key benefits that VPN technologies provide are:
The key benefits that VPN technologies provide are:
- Extend geographic connectivity
- Greatly reduce operational costs when compared to traditional WAN technologies
- Improve productivity
- Provide support for home/remote working
- Integrate well with existing broadband access technologies
They key functions which make VPN technologies secure are the following:
- Authentication – Ensuring the communication is from a trusted source
- Access Control – Preventing unauthorized users from accessing the network
- Confidentiality – Preventing the reading or copying of data as it travels across the public network
- Data integrity – Ensuring the data has not been tampered with as it travels across the public network
There are currently several types of VPN technologies available. These can be broken down into 2 main categories:
- Site to site VPNs
- Client to site (or remote access) VPNs
Site to Site VPNs involve the use of dedicated VPN hardware at each remote site. Remote access VPNs however, utilise a central site VPN concentrator and a software VPN client. The client is installed on the users desktop or laptop and enables the user to establish a secure, encrypted tunnel to the office network. The one exception to this is the SSL VPN which can be fully clientless, utilizing only the user’s web browser to access applications on the organization network. Remote access VPNs allow users to work securely from any location with an Internet connection. For example, from a hotel room, or even a public WiFi hotspot. Network Elements Ltd are able to design and implement IPSEC/SSL VPN remote access solutions based on many vendors product lines and can offer “standalone” VPN solutions or integrated VPN/Firewall solutions.
